Imagine a hiker preparing to leap across a narrow chasm. On the takeoff side, the rock is slick with moss; on the far side, the landing spot is a patch of wet gravel. A seasoned hiker knows that even if the landing spot looks reachable, starting from a slippery surface means you might slip before you ever jump — losing momentum, misjudging your arc, and falling short. Likewise, even if you start from a dry, grippy rock, aiming for a slippery landing means you might not stick the landing. Either way, the result is the same: disappointment at best, injury at worst.

For webmasters, domain-to-domain transitions follow this exact logic. Your “jumping-off point” is the origin page. Your “landing spot” is the destination domain. And the ground beneath each is your protocol — HTTPS for dry, grippy rock; HTTP for slick, unstable footing.
A secure handoff begins with HTTPS on both ends. When a redirect is triggered from an HTTP page, the user’s jump is already compromised. Intermediaries can inspect, modify, or fully hijack the redirect. This is the digital equivalent of slipping at the edge — the user never gets a clean takeoff. Conversely, if the origin is secure but the redirect leads to an HTTP destination, the landing is unsafe. Even with a strong push-off, the user “slides” into an insecure environment where data can be intercepted or altered.
The worst pattern of all remains HTTP → redirect → HTTP — a slippery start and slippery landing — offering no protection at any point in the journey, with a close second being the diagonal patterns HTTPS → redirect → HTTP → redirect → HTTPS or the other diagonal HTTP → redirect → HTTPS.
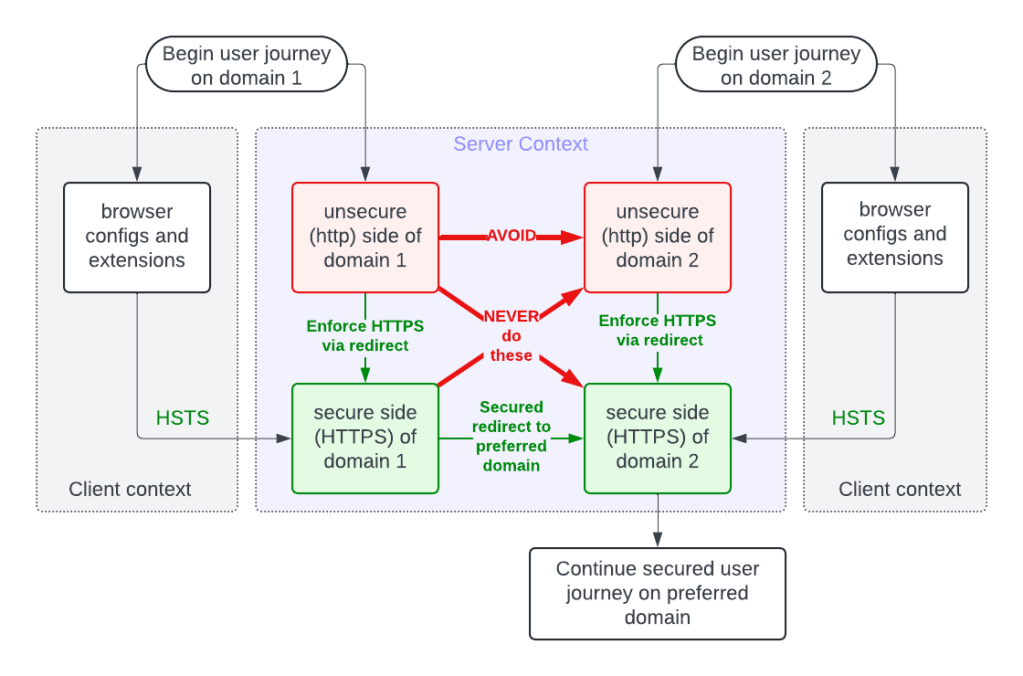
Professional webmasters should ensure secure-start, secure-end transitions:
- Serve all origin pages over HTTPS to guarantee a solid takeoff.
- Redirect only to HTTPS destinations, ensuring a safe, stable landing.
- Implement HSTS to lock browsers into secure mode from the outset.
- Eliminate mixed chains (e.g., HTTPS → HTTP → HTTPS), which reintroduce weak points.
- Audit for legacy HTTP dependencies, especially on older domains or third-party integrations.
Your users trust you to guide them safely across the chasm. Give them firm footing at the start and the end. Choose grippy rock. Choose HTTPS.
Also be a good Scout, and leave the place better than you found it. Setup HSTS on all your feeder domains, not just your primary/driven/promoted domain.